SIEM
Security Information and Events Management (SIEM) aggregates logs from many different elements of the ICT system, correlates them and presents detected threats and incidents in a transparent manner. Thanks to SIEM, threat mitigation for the entire IT area takes place in one place. All information is saved in the logs:
- violations of procedures,
- unauthorized activities from within,
- unauthorized activities from outside the organization,
- errors in used applications,
- wrong configuration,
- outdated backups.

The key factor is risk prevention. The best strategy is to constantly monitor your network for potential vulnerabilities.
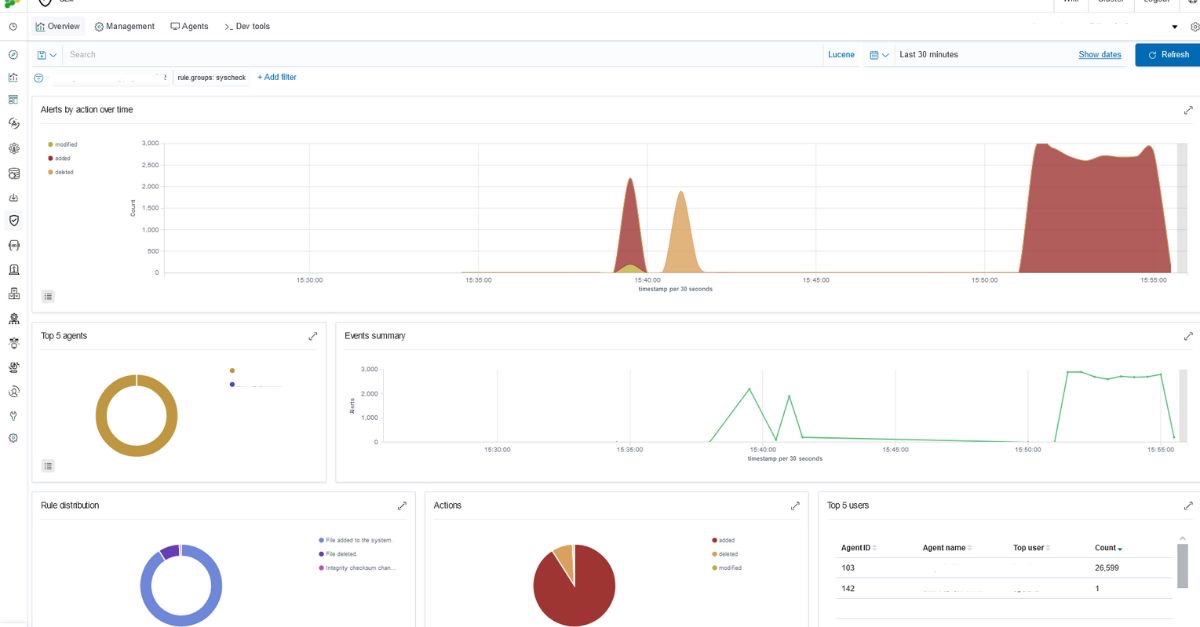
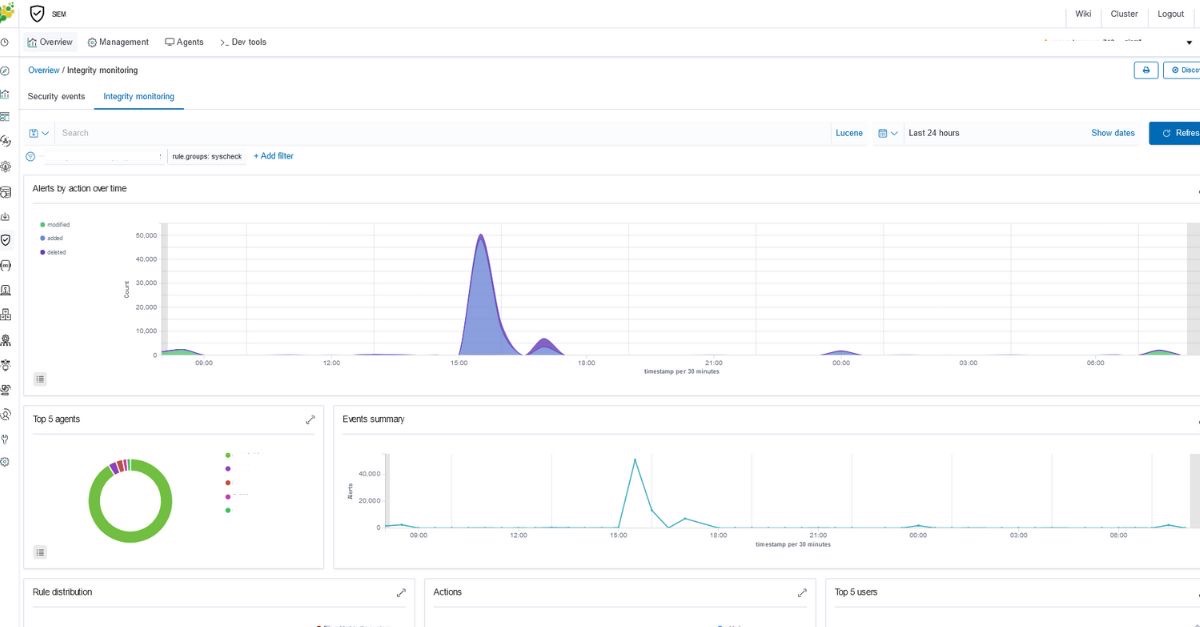
Continuous real-time monitoring, vulnerability detection, event correlation and immediate threat alerts are some of the system’s basic functionalities, and the system’s file integrity monitoring module enables a quick response to an ongoing attack.
The platform recognizes and verifies file system changes to detect the presence of malicious resources. Scanless Vulnerability Detection identifies vulnerable systems and applications by correlating inventory data with Common Vulnerabilities and Exposures. A security configuration assessment is performed that reveals misconfigured systems. If an unusually high number of file creation and file deletion alerts are reported, you may suspect that this is a ransomware attack.
If you want to learn more about the Energy Logserver solution, please contact us.
SOAR (Security Orchestration, Automation and Response) is an advanced business solution that allows organizations to quickly diagnose and automate as many business and IT processes as possible.
SOAR will make the work of administrators easier and safer. It connects to security tools and analyzes IP, URL, files and more. Automation involves the orchestrated use of multiple technologies, tools, and platforms.
Ask for an offer
Would you like to learn more about our offer or have any questions about specific solutions.Please do not hesitate to contact us.