Identity and permission management
IAM (Identity and Access Management) is a dedicated tool for access management. It enables companies to have full control over the assigned data access rights, as well as continuous monitoring of the applications used.
This is done in accordance with organizational requirements and assigned user roles by associating user access and restrictions with established identity. The combination of a modern system that integrates with HR solutions and processes maximizes the security of the organization.
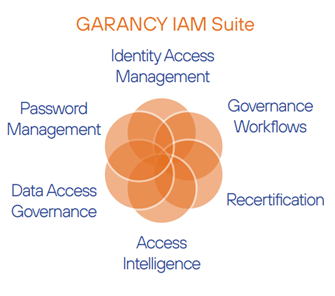
The password management module facilitates access to applications and simplifies the enforcement of IT security policies related to passwords.
Password Reset allows users to reset or modify their own passwords through the web interface.
- Limit helpdesk interventions by delegating password resets to users.
- Increase user productivity as they can reset passwords without waiting for Helpdesk.
Password synchronization allows you to use a single password to access systems and applications. Ensures that a change on one system automatically updates the password for all associated accounts on all other systems.

As the security landscape continues to evolve, IAM may also include additional features such as artificial intelligence (AI), machine learning (ML), and biometric authentication.
Ask for an offer
Would you like to learn more about our offer or have any questions about specific solutions.Please do not hesitate to contact us.